Guide: Social Media Inventory and Intervention

This is a reference guide for how to take inventory of your online social media accounts, how to evaluate their relevance in your life, and how you can take action on them. It's not designed to be an exhaustive resource for how to manage each individual social media account (and this is constantly changing), but rather is a resource for how you can periodically manage them. This is a living document as as this site evolves, so will this guide.
Step 1: Inventory your social media accounts
You might have more social media accounts than you might realize. Here are some you might want to consider. Don't forget, you might have an old or unused account at some of these sites, or you might have an older account you've forgotten about. I once tracked down a neo-Nazi based on tattoos in pictures he posted on a MySpace account years prior. Also keep in mind that you might have created an account just to lurk there to see what was going on or keep tabs on certain accounts.
- X/Twitter
- Threads
- Bluesky
- Mastodon
- Spoutible
- Truth Social
- Gab
- Hive Social
- VKontakte
- MySpace
- etc...
- Tumblr
- Medium
- Substack
- Livejournal
- Ghost
- etc
- Github
- Clubhouse
- Polywork
- Linktree
- etc
- Youtube
- Soundcloud
- Spotify
- Flickr
- 500px
- Vimeo
- etc
- Something Awful
- Google Groups
- etc
- Discord
- Slack
- Line
- Telegram
- etc
- Twitch
- Steam
- Playstation Network
- Xbox Live
- Battle.net
- etc
- Venmo
- Paypal
- Yelp
- Tripadvisor
- CashApp
- KoFi
- Amazon
- etc
Step 2: Consider what you use the account for and what value it brings you
We generally don't sign up for services by accident, and each service we use plays a different role in our lives. For instance, I have a Playstation Network account because it's necessary for me to buy and play games, but I don't really use it for socializing. On the other hand, my Battle.Net account was a pretty big source of my social network at one point in my life, and though I mostly don't use it anymore, it has some sentimental value for me.
In this step, give each account a relevance score from 1 (most relevant) to 5 (least relevant):
- This account is absolutely essential to my business/work/community/mental health/social well-being/communications. I cannot be without it.
- I use this account more or less every day. It's not vital to me, but losing access would hurt.
- I don't use this account day to day but it has relevance to me. I use the account infrequently or I might want to come back to it some day.
- I no longer actively use this account, but I wouldn't want to lose my username/data/features linked to the account.
- I no longer actively use this account and the data there is unimportant to me.
Write this number down as your Relevance score, R.
Step 3: Determine who can use the account to harm you, how likely that harm is, and how bad it might be
Taking inventory of your social media is an opportunity to consider how this account may be used to harm you, and who might use it to harm you. "Harm" can be any negative outcome, ranging from police surveillance to online harassment to exploitation of your data for ad targeting, tracking, or AI training. For instance, old social media posts could be taken out of context and be used to defame you.
Consider the likelihood of these harms actually happening and rank the likelihood from 1 (least likely) to 5 (most likely). You'll probably come up with a couple ways that the account can be used to harm you, just pick the number that feels best for the account—it's not necessary to be super scientific. We'll call this your Likelihood score, L.
Do the same for the severity of those harms, where 1 is least severe and 5 is most severe. A score of 5 would represent a serious threat to life, liberty or livelihood; a 1 would be almost unnoticeable. Call this score your Severity score, S.
Step 4: Compute your risk index
If you've done the above steps, you'll have three scores: R, L, and S. Multiply these together to get the Risk Index: I = R x L x S. The higher the number, the more serious it is to take action with your account. I also like to factor in the relevance score: if R = 4 or 5 (meaning it's not relevant to me at all), then I don't have to think much—I can usually just delete the account.
Step 5: Determine what actions to take and why
For each account you're reviewing, think about what actions you want to take and why. These actions can loosely map to the relevance score you assessed in Step 2. They can include adverse actions like:
- account deletion;
- downloading your data and deactivating the account;
- deleting the account but creating a new one to squat your username;
- turning on two-factor authentication (2FA);
- purging the account data;
- purging data older than a certain age;
- cleaning up contacts/friends/followers/following;
- locking or turning the account private;
- ignoring the account;
- deleting the apps from your phone;
- blocking the IP in your DNS or
hostsfile; - removing public references to it.
There are many reasons why you might want to take adverse actions on an account. You can do so because you no longer align with the company's values and you want to deny them access to your data. You may want to sever ties with the people you once networked with there, for instance people who had a bad influence on you. Or you may just want to minimize your digital footprint and make it harder for a malicious actor to use your online presence against you.
On the other hand, there may be neutral or positive actions you can take, too. For instance, some of my tweets have been cited in print. Though I had already deleted some of them, I'd like to not contribute more than I need to to link rot. So while I don't use Twitter anymore and have no intention to in the future, I have curated my posts and decided to retain the remainder as a historical and reference record. So some things you might want to do to curate your digital presence can include:
- retaining posts for public archival purposes;
- migrating posts to a preferred social network;
- running your own server on a federated network;
- publishing searchable archives of your data or working with librarians/archivists in your area to help preserve these records;
- building intentional community on a social network;
- blocking malicious actors;
- reflecting on your intentions and usage habits and changing behaviors accordingly;
- optimizing the account for your preferences/benefit.
Step 5: Take action
If you've done your risk inventory like I've described, you should end up with something like this. In fact, I've made this template public on Google Sheets for you to copy or download and use as you'd like. And I'm working on a privacy-preserving app that I'll embed here for your use.
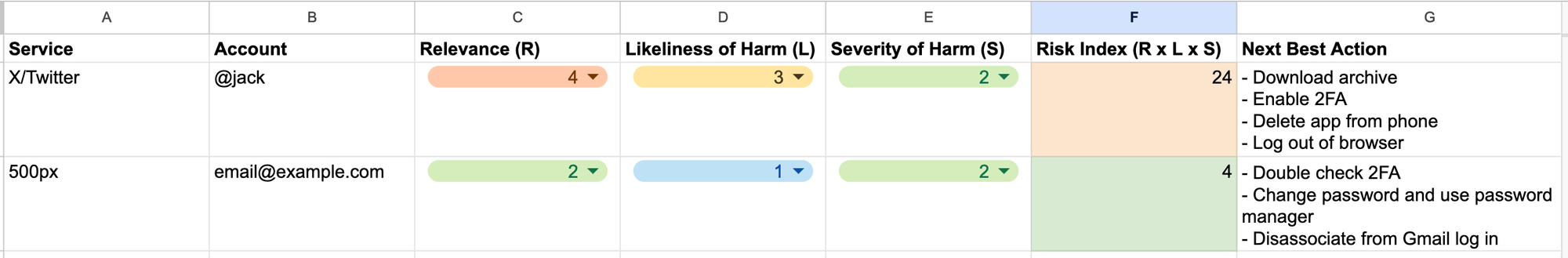
Each account has a different user flow for taking these actions, and these flows change frequently. However, I'll try to keep some fresh instructions for the most common sites here.
X/Twitter
- Download your archive (web)
- In the menu on the left, click "Settings and Privacy". Depending on your account, this may be buried under "More".
- Under "Your account", click "Download an archive of your data".
- Enter your password, select any options, and wait for the download to be prepared.
- You'll receive a notifcation on-platform and an email when the archive is ready for download.
- Download this (it can be very large) and store it somewhere safe.
- Enable two-factor authentication
- On the left, click "Settings and Privacy".
- Select "Security and Account Access" then choose "Security".
- Select "Two-factor Authentication" and choose a method. Note: 2FA over text message is not recommended and not considered secure.
- Copy or print your backup codes and store them somewhere safe.
- Set account private
- Click "Settings and Privacy" and choose "Your account".
- Select "Account information" and enter your password.
- Select "Protected posts" and then toggle on "Protect posts". You can also choose "Protect videos" and can turn off photo tagging.
- Delete account
- Click "Settings and Privacy" and then "Your account".
- Choose "Deactivate your account".
- On the next screen, carefully read the warnings and click "Deactivate" if you agree.
- You have 30 days to change your mind and reactivate the account. After 30 days your user name will be released and others can claim it.
Facebook/Threads/Instagram
- Download your archive (web)
- Click your profile icon in the top right and choose "Settings & privacy".
- On the left, under "Accounts center", click "See more in Accounts Center".
- Choose "Your information and permissions".
- Click "Download your information", select the options, and wait.
- You'll receive a notification on-platform and an email when the download is ready.
- Enable 2FA or change password
- Go to the "Accounts Center" as above.
- Choose "Password and security" and choose the relevant option.
- Deactivate account
- Go to the "Accounts Center" as above.
- Choose "Personal Details" and then "Account ownership and control".
- Choose to deactivate or delete. Deactivation will preserve your ability to use Messenger.
Thanks for taking a look. More is to come!